3\Test
VMConAWS to SDDC 같은 NSX끼리는 VPN 연결구성 가능합니다.
VMConAWS to TGW on VPN(AWS)도 VPN 가능합니다.
https://www.gilles.cloud/2019/03/deploy-vmc-route-based-vpn-with-api.html
별로 VGW나 Tier GW없어도 host간 VPN설정이 가능합니다. libreswan으로 ipsec vpn site to site 구성 (policy base vpn, without vti)
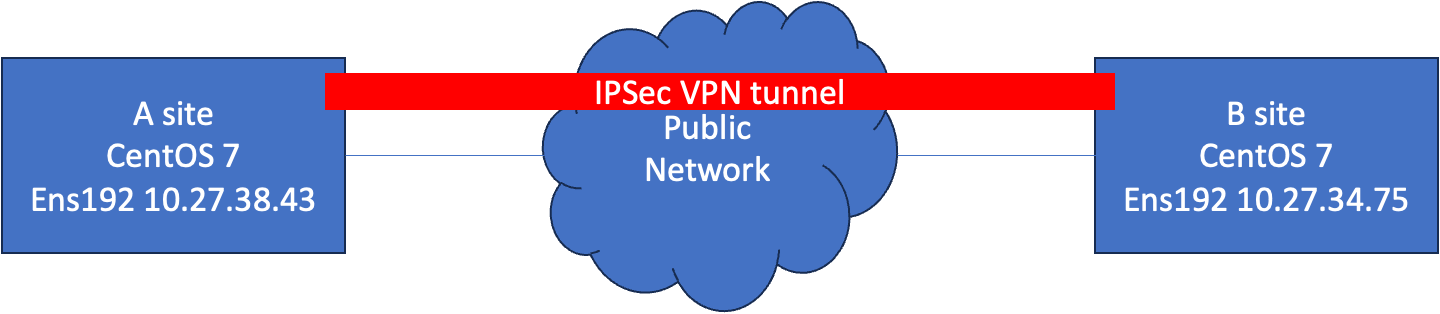
A Site / B site ipsec status
[root@bb-cent-78 ~]# ipsec status
000 using kernel interface: netkey
000 interface lo/lo ::1@500
000 interface lo/lo 127.0.0.1@4500
000 interface lo/lo 127.0.0.1@500
000 interface ens192/ens192 10.27.38.43@4500
000 interface ens192/ens192 10.27.38.43@500
IPsec VPN configure on A/B site
conn mytunnel
left=10.27.38.43
leftrsasigkey=0sAwEAAcscZELWilQ+72HPQ5oWN0BtEcqE5XExzl/pOr
right=10.27.34.75
rightrsasigkey=0sAwEAAa3euvKD9Bjms+dGwvZRyu+VqDBE5K9RgLopBP0ETonZn
authby=rsasig
# load and initiate automatically
auto=start
leftsubnet=10.27.38.0/20
rightsubnet=10.27.34.0/20
ipsec 추가
[root@bb-cent-78 ipsec.d]# ipsec auto --add mytunnel
002 "mytunnel": terminating SAs using this connection
002 "mytunnel" #59: deleting state (STATE_QUICK_R2) and sending notification
005 "mytunnel" #59: ESP traffic information: in=0B out=0B
002 "mytunnel" #58: deleting state (STATE_MAIN_R3) and sending notification
002 "mytunnel": deleting non-instance connection
002 added connection description "mytunnel"
[root@bb-cent-78 ipsec.d]# ipsec auto --up mytunnel
002 "mytunnel" #62: initiating Quick Mode RSASIG+ENCRYPT+TUNNEL+PFS+UP+IKEV1_ALLOW+IKEV2_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW+ESN_NO {using isakmp#60 msgid:b75d8d8e proposal=defaults pfsgroup=MODP2048}
117 "mytunnel" #62: STATE_QUICK_I1: initiate
004 "mytunnel" #62: STATE_QUICK_I2: sent QI2, IPsec SA established tunnel mode {ESP=>0x051a9066 <0x83bc0dc8 xfrm=AES_CBC_128-HMAC_SHA1_96 NATOA=none NATD=none DPD=passive}
[root@bb-cent-78 ipsec.d]#
[root@bb-cent-78 ipsec.d]# ipsec whack --trafficstatus
006 #61: "mytunnel", type=ESP, add_time=1698818707, inBytes=0, outBytes=0, id='10.27.34.75'
006 #62: "mytunnel", type=ESP, add_time=0, inBytes=0, outBytes=0, id='10.27.34.75'
ipsec tunnel 활성화
root@bb-cent-78 ipsec.d]# ipsec auto --up mytunnel
002 "mytunnel" #62: initiating Quick Mode RSASIG+ENCRYPT+TUNNEL+PFS+UP+IKEV1_ALLOW+IKEV2_ALLOW+SAREF_TRACK+IKE_FRAG_ALLOW+ESN_NO {using isakmp#60 msgid:b75d8d8e proposal=defaults pfsgroup=MODP2048}
117 "mytunnel" #62: STATE_QUICK_I1: initiate
004 "mytunnel" #62: STATE_QUICK_I2: sent QI2, IPsec SA established tunnel mode {ESP=>0x051a9066 <0x83bc0dc8 xfrm=AES_CBC_128-HMAC_SHA1_96 NATOA=none NATD=none DPD=passive}
on A site, Ping to B site
[root@bb-cent-78 ipsec.d]# ping 10.27.34.75
PING 10.27.34.75 (10.27.34.75) 56(84) bytes of data.
64 bytes from 10.27.34.75: icmp_seq=1 ttl=64 time=0.551 ms
64 bytes from 10.27.34.75: icmp_seq=2 ttl=64 time=0.483 ms
64 bytes from 10.27.34.75: icmp_seq=3 ttl=64 time=0.607 ms
64 bytes from 10.27.34.75: icmp_seq=4 ttl=64 time=0.498 ms
64 bytes from 10.27.34.75: icmp_seq=5 ttl=64 time=0.625 ms
64 bytes from 10.27.34.75: icmp_seq=6 ttl=64 time=0.565 ms
64 bytes from 10.27.34.75: icmp_seq=7 ttl=64 time=0.673 ms
64 bytes from 10.27.34.75: icmp_seq=8 ttl=64 time=0.621 m
checked ESP packet on B site
root@bb-cent-78 ipsec.d]# tcpdump -n -i ens192
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on ens192, link-type EN10MB (Ethernet), capture size 262144 bytes
06:09:49.960021 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 392894662:392894858, ack 1572104445, win 333, options [nop,nop,TS val 150523133 ecr 3915421887], length 196
06:09:49.960349 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 196:424, ack 1, win 333, options [nop,nop,TS val 150523133 ecr 3915421887], length 228
06:09:49.960507 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 424:620, ack 1, win 333, options [nop,nop,TS val 150523134 ecr 3915421887], length 196
06:09:49.960633 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 620:816, ack 1, win 333, options [nop,nop,TS val 150523134 ecr 3915421887], length 196
06:09:50.030482 ARP, Request who-has 192.168.10.13 tell 192.168.10.2, length 46
06:09:50.154428 ARP, Request who-has 10.27.44.160 tell 10.27.47.254, length 46
06:09:50.198031 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 0, win 2047, options [nop,nop,TS val 3915422164 ecr 150523096], length 0
06:09:50.198067 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 816:1244, ack 1, win 333, options [nop,nop,TS val 150523371 ecr 3915422164], length 428
06:09:50.229144 ARP, Request who-has 10.27.40.167 tell 10.27.46.186, length 46
06:09:50.237889 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 424, win 2041, options [nop,nop,TS val 3915422205 ecr 150523133], length 0
06:09:50.237916 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 1244:1716, ack 1, win 333, options [nop,nop,TS val 150523411 ecr 3915422205], length 472
06:09:50.237937 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 816, win 2035, options [nop,nop,TS val 3915422205 ecr 150523134], length 0
06:09:50.238143 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 1716:2216, ack 1, win 333, options [nop,nop,TS val 150523411 ecr 3915422205], length 500
06:09:50.238310 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 2216:2428, ack 1, win 333, options [nop,nop,TS val 150523411 ecr 3915422205], length 212
06:09:50.238489 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 2428:2640, ack 1, win 333, options [nop,nop,TS val 150523411 ecr 3915422205], length 212
06:09:50.412584 ARP, Request who-has 10.27.47.254 tell 10.27.45.43, length 46
06:09:50.431869 IP 10.27.32.141.netbios-ns > 10.27.47.255.netbios-ns: NBT UDP PACKET(137): QUERY; REQUEST; BROADCAST
06:09:50.477008 ARP, Request who-has 192.168.10.1 tell 192.168.10.11, length 46
06:09:50.517329 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 1244, win 2041, options [nop,nop,TS val 3915422482 ecr 150523371], length 0
06:09:50.517379 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 2640:3248, ack 1, win 333, options [nop,nop,TS val 150523690 ecr 3915422482], length 608
06:09:50.517410 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 2640, win 2019, options [nop,nop,TS val 3915422482 ecr 150523411], length 0
06:09:50.517629 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 3248:3748, ack 1, win 333, options [nop,nop,TS val 150523691 ecr 3915422482], length 500
06:09:50.517808 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 3748:3960, ack 1, win 333, options [nop,nop,TS val 150523691 ecr 3915422482], length 212
06:09:50.517967 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 3960:4172, ack 1, win 333, options [nop,nop,TS val 150523691 ecr 3915422482], length 212
06:09:50.518124 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 4172:4384, ack 1, win 333, options [nop,nop,TS val 150523691 ecr 3915422482], length 212
06:09:50.631494 ARP, Request who-has 10.27.33.155 tell 10.27.44.19, length 46
06:09:50.664801 ARP, Request who-has 10.27.33.180 tell 10.27.47.254, length 46
06:09:50.724134 IP 10.27.38.43 > 10.27.34.75: ESP(spi=0x051a9066,seq=0x16), length 132
06:09:50.724197 IP 10.27.38.43 > 10.27.34.75: ICMP echo request, id 5919, seq 5, length 64
06:09:50.724243 IP 10.27.34.75 > 10.27.38.43: ESP(spi=0x83bc0dc8,seq=0x16), length 132
06:09:50.797857 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 3248, win 2038, options [nop,nop,TS val 3915422764 ecr 150523690], length 0
06:09:50.797886 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 4384:5136, ack 1, win 333, options [nop,nop,TS val 150523971 ecr 3915422764], length 752
06:09:50.797909 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 4384, win 2020, options [nop,nop,TS val 3915422764 ecr 150523691], length 0
06:09:50.798114 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 5136:5636, ack 1, win 333, options [nop,nop,TS val 150523971 ecr 3915422764], length 500
06:09:50.798276 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 5636:5848, ack 1, win 333, options [nop,nop,TS val 150523971 ecr 3915422764], length 212
06:09:50.798434 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 5848:6060, ack 1, win 333, options [nop,nop,TS val 150523971 ecr 3915422764], length 212
06:09:50.798609 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 6060:6272, ack 1, win 333, options [nop,nop,TS val 150523972 ecr 3915422764], length 212
06:09:50.926008 ARP, Request who-has 192.168.10.13 tell 192.168.10.4, length 46
06:09:51.035312 ARP, Request who-has 192.168.10.13 tell 192.168.10.2, length 46
06:09:51.078193 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 5136, win 2036, options [nop,nop,TS val 3915423045 ecr 150523971], length 0
06:09:51.078229 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 6272:6716, ack 1, win 333, options [nop,nop,TS val 150524251 ecr 3915423045], length 444
06:09:51.078270 IP 10.217.216.87.50038 > 10.27.34.75.ssh: Flags [.], ack 6272, win 2048, options [nop,nop,TS val 3915423045 ecr 150523971], length 0
06:09:51.078447 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 6716:7216, ack 1, win 333, options [nop,nop,TS val 150524251 ecr 3915423045], length 500
06:09:51.078570 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 7216:7428, ack 1, win 333, options [nop,nop,TS val 150524252 ecr 3915423045], length 212
06:09:51.078686 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 7428:7640, ack 1, win 333, options [nop,nop,TS val 150524252 ecr 3915423045], length 212
06:09:51.078801 IP 10.27.34.75.ssh > 10.217.216.87.50038: Flags [P.], seq 7640:7852, ack 1, win 333, options [nop,nop,TS val 150524252 ecr 3915423045], length 212
06:09:51.188081 IP 10.27.32.141.netbios-ns > 10.27.47.255.netbios-ns: NBT UDP PACKET(137): QUERY; REQUEST; BROADCAST
06:09:51.222011 ARP, Request who-has 10.27.42.99 tell 10.27.47.253, length 46
06:09:51.239292 ARP, Request who-has 10.27.40.167 tell 10.27.46.186, length 46
'IT' 카테고리의 다른 글
| DNS resolve 해보기. (0) | 2023.11.15 |
|---|---|
| quagga bgp (1) | 2023.11.01 |
| Add to interface in Management Profile on Paloalto (0) | 2021.11.20 |
| EVE-NG web consol에 login이 안될때.. (1) | 2020.09.19 |
| Cisco Switch 비교 (1) | 2020.02.17 |

